|
Collecting System State Information | |||||||||||||||
|
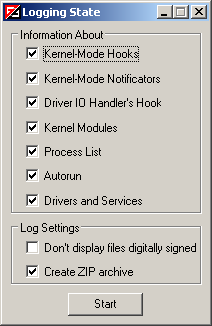
The File – Logging State menu item invokes the Logging State dialog box where you can collect all information on system state and save it to a file. The following data can be obtained: hooks of SSDT, Shadow SSDT, EAT, IDT and SYSENTER (the Kernel-Mode Hooks flag), list of installed kernel mode notificators (the Kernel-Mode Notificators flag), list of IRP and FastIO hooks (the Driver IO Handler Hook flag), list of kernel modules (the Kernel Modules flag), list of processes (the Process List flag), list of registered in registry drivers and services (the Drivers and Services flag), list of autoruns (the Autorun flag). Moreover it’s possible to exclude information on files which are digitally signed (the Don’t display files digitally signed flag) and add scanning report in the form of a Zip archive (the Create ZIP archive flag). The output file can be sent to the technical support service. To do so, you should save *.html report and launch the SendLogs utility located in the Vba32 antivirus installation folder.
| |||||||||||||||